Recent Score: out of 30.
Take the Test again Go HomeResources
1
AWS CloudTrail
When you want to log what actions various IAM users are taking in your AWS account.
2
Pci dss level-1 faqs
PCI Compliant AWS Services - Ensure the right steps are taken during application development for PCI Compliance
3
AWS shield - ddos attack protection
One of the first techniques to mitigate DDoS attacks is to minimize the surface area that can be attacked thereby limiting the options for attackers and allowing you to build protections in a single place. We want to ensure that we do not expose our application or resources to ports, protocols or applications from where they do not expect any communication. Thus, minimizing the possible points of attack and letting us concentrate our mitigation efforts. In some cases, you can do this by placing your computation resources behind; Content Distribution Networks (CDNs), Load Balancers and restricting direct Internet traffic to certain parts of your infrastructure like your database servers. In other cases, you can use firewalls or Access Control Lists (ACLs) to control what traffic reaches your applications.
4
AWS Secure transfer acceleration examples
Secure File Transfer Acceleration
5
AWS DMS
AWS Database Migration Service helps you migrate databases to AWS quickly and securely. The source database remains fully operational during the migration, minimizing downtime to applications that rely on the database. The AWS Database Migration Service can migrate your data to and from most widely used commercial and open source databases.
6
AWS Snowball
Snowball is a petabyte-scale data transport solution that uses secure appliances to transfer large amounts of data& into and out of the AWS cloud. Using Snowball addresses common challenges with large-scale data transfers including high network costs, long transfer times, and security concerns. Transferring data with Snowball is simple, fast, secure, and can be as little as one-fifth the cost of high-speed Internet.
7
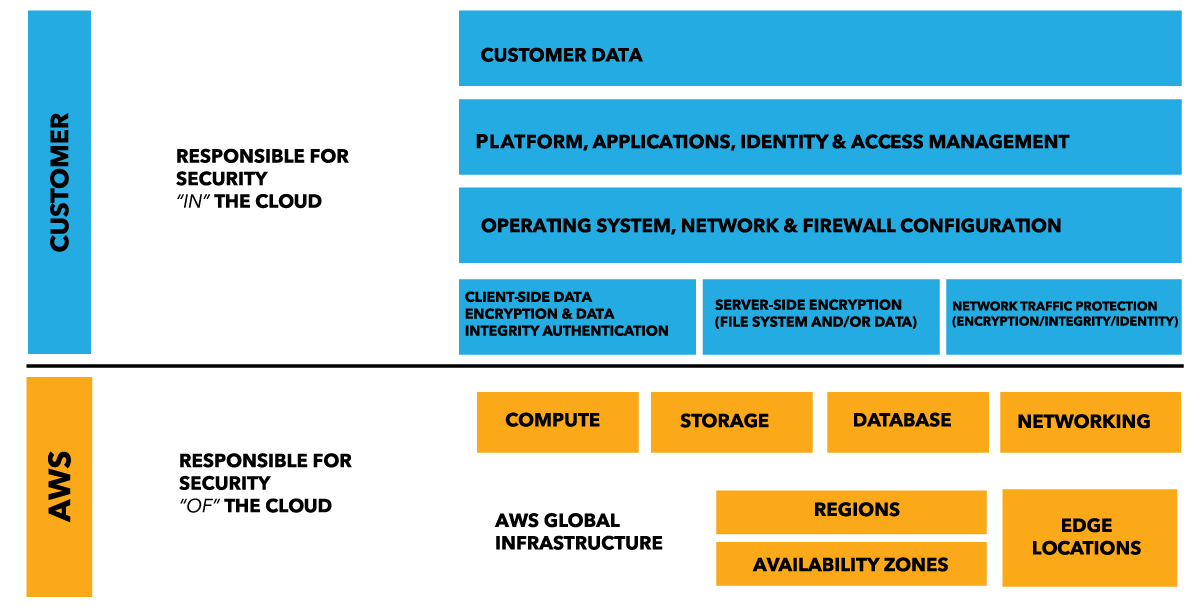
AWS Shared Responsibility Model
It is AWS responsibility to secure Edge locations and decommission the data.AWS responsibility “Security of the Cloud” - AWS is responsible for protecting the infrastructure that runs all of the services offered in the AWS Cloud. This infrastructure is composed of the hardware, software, networking, and facilities that run AWS Cloud services.
8
AWS VPC Security Groups
Security groups acts as a virtual firewall for your instance to control inbound and outbound traffic. When you launch an instance in a VPC, you can assign up to five security groups to the instance. Security groups act at the instance level, not the subnet level. Therefore, each instance in a subnet in your VPC could be assigned to a different set of security groups. If you don't specify a particular group at launch time, the instance is automatically assigned to the default security group for the VPC.
9
Ddos attack protection
One of the first techniques to mitigate DDoS attacks is to minimize the surface area that can be attacked thereby limiting the options for attackers and allowing you to build protections in a single place. We want to ensure that we do not expose our application or resources to ports, protocols or applications from where they do not expect any communication. Thus, minimizing the possible points of attack and letting us concentrate our mitigation efforts. In some cases, you can do this by placing your computation resources behind Content DistributionNetworks (CDNs), Load Balancers and restricting direct Internet traffic to certain parts of your infrastructurelike your database servers. In other cases, you can use firewalls or Access Control Lists (ACLs) to control what traffic reaches your applications.
10
AWS trusted advisor
An online resource to help you reduce cost, increase performance, and improve security by optimizing your AWS environment, Trusted Advisor provides real time guidance to help you provision your resources following AWS best
11
AWS pen testing
You need to take authorization from AWS before doing a penetration test on EC2 instances.
12
VPC Security Groups and Network Access Control List
Security groups acts as a virtual firewall for your instance to control inbound and outbound traffic. Network access control list (ACL) is an optional layer of security for your VPC that acts as a firewall for controlling traffic in and out of one or more subnets.
13
Security in AWS using Network Security Groups
When you define security rules for EC2 Instances, you give a name, description and write the rules for the security group
14
AWS Trust Advisor

15
Domain Name Systems
Domain name system servers act as a "third party" that provides the service of converting common language domain names to IP addresses (which are required for a web browser to properly make a request for web content).
16
AWS inspector introduction
Amazon Inspector enables you to analyze the behaviour of your AWS resources and helps you to identify potential security issues. Using Amazon Inspector, you can define a collection of AWS resources that you want to include in an assessment target. You can then create an assessment template and launch a security assessment run of this target.
17
AWS VPC ACLs
A network access control list (ACL) is an optional layer of security for your VPC that acts as a firewall for controlling traffic in and out of one or more subnets. You might set up network ACLs with rules similar to your security groups in order to add an additional layer of security to your VPC.
18
AWS Shared Responsibility Model
It is AWS responsibility to secure Edge locations and decommission the data.
AWS responsibility “Security of the Cloud” - AWS is responsible for protecting the infrastructure that runs all of the services offered in the AWS Cloud. This infrastructure is composed of the hardware, software, networking, and facilities that run AWS Cloud services.
19
VPC Endpoint
A VPC endpoint enables you to privately connect your VPC to supported AWS services and VPC endpoint services powered by PrivateLink without requiring an internet gateway, NAT device, VPN connection, or AWS Direct Connect connection. Instances in your VPC do not require public IP addresses to communicate with resources in the service. Traffic between your VPC and the other service does not leave the Amazon network.
20
AWS CloudTrail
When you want to log what actions various IAM users are taking in your AWS account.
21
AWS VPC
Amazon Virtual Private Cloud (Amazon VPC) lets you provision a logically isolated section of the AWS Cloud where you can launch AWS resources in a virtual network that you define. You have complete control over your virtual networking environment, including selection of your own IP address range, creation of subnets, and configuration of route tables and network gateways.
22
AWS CloudTrail
You can identify who or what took which action, what resources were acted upon, when the event occurred, and other details to help you analyze and respond to activity in your AWS account. Optionally, you can enable AWS CloudTrail Insights on a trail to help you identify and respond to unusual activity.
23
AWS Acceptable Use Policy
The Acceptable Use Policy describes prohibited uses of the web services offered by Amazon Web Services, Inc. and its affiliates and the website located at http://aws.amazon.com .
24
AWS VPN; AWS Direct Connect
A virtual private network extends a private network across a public network and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network. AWS Direct Connect is a cloud service solution that makes it easy to establish a dedicated network connection from your premises to AWS.
26
AWS KMS master-key and AWS KMS stored customer key
The two encryption key options are available in the AWS web console when you are uploading a new object with the upload wizard are the Amazon S3 master-key and the AWS KMS master-key options. The two encryption key options are available in the AWS web console when you are uploading a new object with the upload wizard are the Amazon S3 master-key and the AWS KMS master-key options.
27
Include New Services in Incident Response Plan
Your incident response plan not only needs to be used — it also needs to be updated with new services.
28
AWS CloudFront
CloudFront allows you to cache content at edge locations. When a request is made for that content, the request is sent to an edge location (not your application's hardware), so the edge locations absorb DDoS attacks and protect your underlying hardware.