Question
Time left
Score
0
What is the answer to this questions?
A
Choice 1
B
Choice 2
C
Choice 3
D
Choice 4
0
Security and Compliance Exam Details (25%)
- Define the AWS shared responsibility model
- Define AWS Cloud security and compliance concepts
- Identify AWS access management capabilities
- Identify resources for security support
1
Access Keys
Access keys are long-term credentials for an IAM user or the AWS account root user. You can use access keys to sign programmatic requests to the AWS CLI or AWS API.
You must provide your AWS access keys to make programmatic calls to AWS or to use the AWS Command Line Interface or AWS Tools for PowerShell. When you create your access keys, you create the access key ID (for example, AKIAIOSFODNN7EXAMPLE) and secret access key (for example, wJalrXUtnFEMI/EXAMPLEKEY) as a set. The secret access key is available for download only when you create it. If you don't download your secret access key or if you lose it, you must create a new one.
2
Principle of Least Privileged
When you create IAM policies, follow the standard security advice of granting the least privilege, or granting only the permissions required to perform a task. Determine what users (and roles) need to do, and then craft policies that allow them to perform only those tasks.
3
Amazon Macie
Amazon Macie is a fully managed data security and data privacy service that uses machine learning and pattern matching to discover and protect your sensitive data in AWS.
4
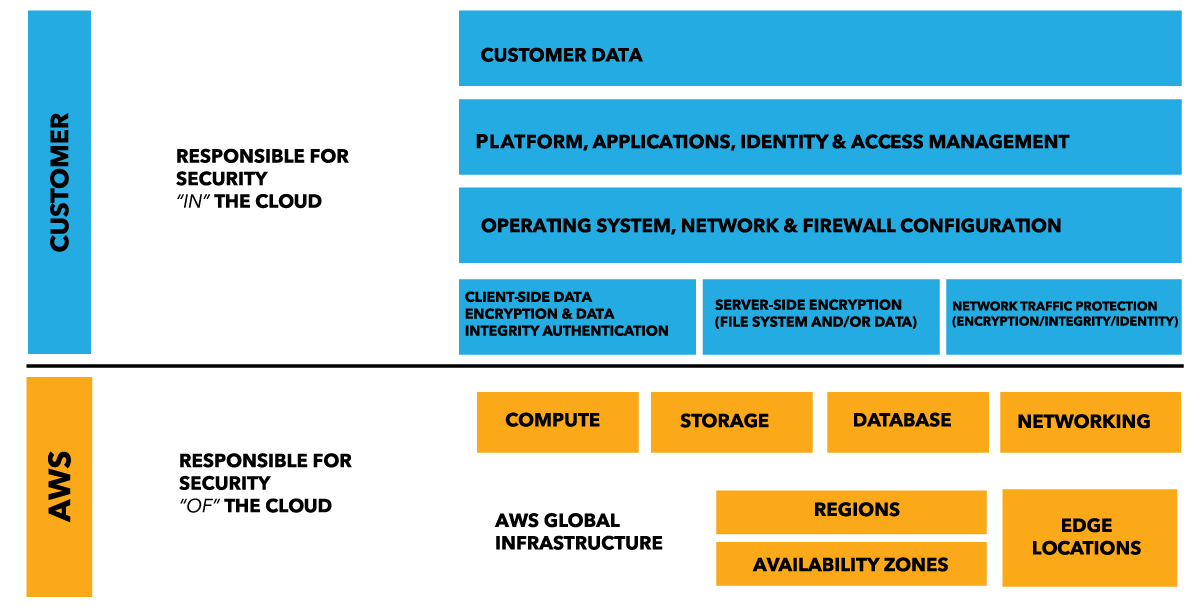
Shared Resposibilty Model: Security
AWS is in charge of physically securing compute resources, as it is part of the infrastructure that runs all of the services offered in the AWS Cloud. Network patching is one of AWS's responsibilities, as it is connected to the infrastructure that AWS handles. Disk disposal is one of AWS's responsibilities, as it is connected to the infrastructure, which AWS handles.
5
AWS Multi-Factor Authentication (MFA)
AWS Multi-Factor Authentication (MFA) is a simple best practice that adds an extra layer of protection on top of your user name and password. With MFA enabled, when a user signs in to an AWS Management Console, they will be prompted for their user name and password (the first factor—what they know), as well as for an authentication code from their AWS MFA device (the second factor—what they have). Taken together, these multiple factors provide increased security for your AWS account settings and resources.
6
Security Group
A security group acts as a virtual firewall for your instance to control inbound and outbound traffic. When you launch an instance in a VPC, you can assign up to five security groups to the instance. Security groups act at the instance level, not the subnet level. Therefore, each instance in a subnet in your VPC can be assigned to a different set of security groups.
7
Network Load Balancer
Network Load Balancer is best suited for load balancing of Transmission Control Protocol (TCP), User Datagram Protocol (UDP) and Transport Layer Security (TLS) traffic where extreme performance is required. Operating at the connection level (Layer 4), Network Load Balancer routes traffic to targets within Amazon Virtual Private Cloud (Amazon VPC) and is capable of handling millions of requests per second while maintaining ultra-low latencies.
8
IAM Groups
By creating an IAM group, all alike users can be managed all at one time. Once the permissions are defined within the policy, it can be attached to the IAM group, allowing them access to the resources/services stated within the policy.
9
AWS CloudTrail
AWS CloudTrail is a service that enables governance, compliance, operational auditing, and riskauditing of your AWS account. With CloudTrail, you can log, continuously monitor, and retain account activity related to actions across your AWS infrastructure. CloudTrail provides event history of your AWS account activity, including actions taken through the AWS Management Console, AWS SDKs, command line tools, and other AWS services. This event history simplifies security analysis, resource change tracking, and troubleshooting
10
Shared Responsibility: Securing Edge Locations
It is AWS responsibility to secure Edge locations and decommission the data. AWS responsibility “Security of the Cloud” - AWS is responsible for protecting the infrastructure that runs all of the services offered in the AWS Cloud. This infrastructure is composed of the hardware, software, networking, and facilities that run AWS Cloud services.
11
What checksums does Amazon S3 employ to detect data corruption?
Amazon S3 uses a combination of Content-MD5 checksums and cyclic redundancy checks (CRCs) to detect data corruption.
Amazon S3 performs these checksums on data at rest and repairs any corruption using redundant data.
In addition, the service calculates checksums on all network traffic to detect corruption of data packets when storing or retrieving data.
12
In VPC with private and public subnets, database servers should ideally be launched
into which subnet?
With private and public subnets in VPC, database servers should ideally launch into private
subnets.
13
Mention what the security best practices for Amazon EC2 are?
For secure Amazon EC2 best practices, follow the following steps.
- Use AWS identity and access management to control access to your AWS resources
- Restrict access by allowing only trusted hosts or networks to access ports on your
instance
- Review the rules in your security groups regularly
- Only open up permissions that you require
- Disable password-based login, for example, launched from your AMI
-
14
What is meant by subnet?
A large section of IP Address divided into chunks is known as subnets.
15
Can you establish a Peering connection to a VPC in a different region?
Yes, we can establish a peering connection to a VPC in a different region. It is called
inter-region VPC peering connection.